C-UAS
Counter-UAS (C-UAS) is essential for identifying and neutralizing drone threats, including those with hostile motives to non-malicious but hazardous scenarios like emergencies or flyaways. By integrating C-UAS with UTM platforms like Unifly, defence and security agencies can differentiate between conformant and potentially malicious or dangerous drones.
TRUSTED BY INDUSTRY LEADERS
Challenges in Differentiating Drones Threats
Rising Drone Use and Security Challenges
As drone technology advances and expands, the challenge of safeguarding against unauthorised or malicious use intensifies.
Differentiating Remote-ID
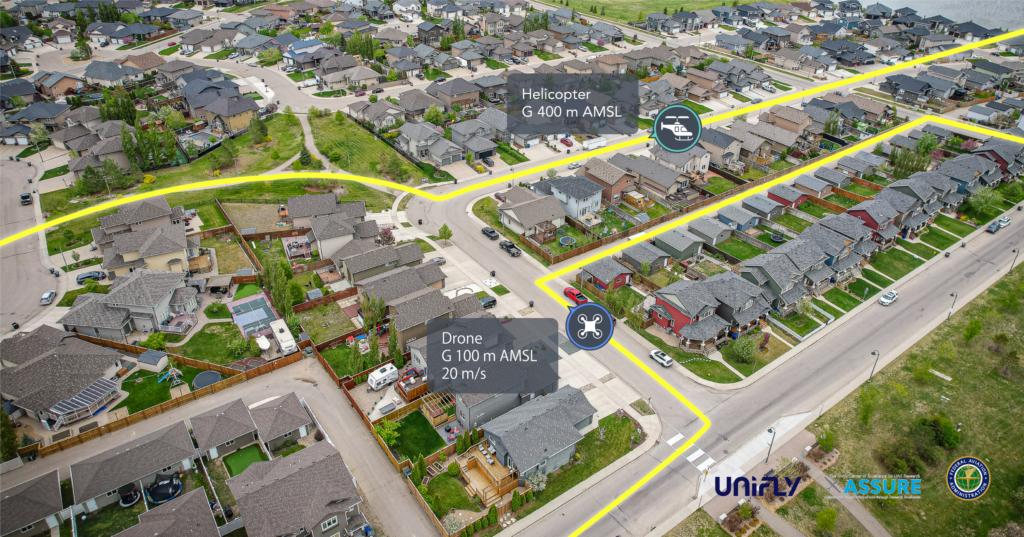
Current C-UAS Systems are capable of detecting drone presence but lack the capability to differentiate between those adhering to regulations, indicated by remote ID, and those potentially posing threats without remote ID.
Identifying False Positives
Even drones that utilise remote ID can pose a security or safety threat, known as false positives. It’s crucial to distinguish drones that are truly following flight regulations from those that might intend harm or accidentally stray off course, such as in emergencies or due to losing control.

Unifly's Solution to C-UAS Challenges
Remote-ID Exchange
Unifly’s platform gathers remote-ID information from drones through various mechanisms and supplies this data to C-UAS systems, enabling C-UAS systems to distinguish between drones with and without remote-ID.
Advanced Conformance Monitoring
Enhanced Situational Awareness
Proven C-UAS/Surveillance Radar Integrations
Integration Using Industry Standards
Products Utilized in C-UAS Solution
For Drone AND UAM/AAM OPERATORS
- Prepare: Register UAS with Remote ID devices for clear identification.
- Plan and Validate: Plan flights within approved volumes and ensure compliance with regulations.
- Fly: Enhance situational awareness during operations.
- Resolve: Provide Non-Conformance alerts to UAS pilots for immediate action.
For SUPERVISORS
- Authenticate: Secure login via SSO.
- Authorize: Approve Flight Plans as required.
- Supervise: Monitor all UAS activities within their responsibility area, ensuring security and compliance.
Api capabilities
- Operator API: Ensures seamless drone integration for efficient operations.
- Platform API: Facilitates data exchange between the UTM platform and C-UAS systems, including Remote-ID positions, conformance alerts, and flight authorization details.
Ready to elevate your airspace?